# HPE Ezmeral Container Platform - Role-Based Access Control
Role-based access control (RBAC), also known as role-based security, is a framework that restricts system access. It does so, by setting permissions and privileges to enable access to authorized users. Most organizations use role-based access control to provide their employees with varying levels of access based on their roles and responsibilities. This protects sensitive data and ensures employees can only access information and perform actions they need to do their duties.
# Users and Roles in HPE Ezmeral Container Platform
The HPE Ezmeral Container Platform provides multi-tenant hybrid cloud platform. This multi-tenant platform is based on Role-based access control. Some of the user- and tenant-related considerations to be resolved when planning/maintaining your deployment include:
Tenants: The number of tenants and the function(s) each tenant performs will determine how many users with the Tenant Administrator role will be needed and, by extension, the number of users with the Tenant Member role will be needed for each tenant. The reverse is also true, since the number and functions of users needing to run jobs can influence how you define tenants. For example, different levels of confidentiality may mandate separate tenants.
Job functions: The specific work performed by a given user will directly impact the role they receive. For example, a small organization may designate a single user as the Tenant Administrator for multiple tenants, while a large organization may designate multiple Tenant Administrators per tenant.
Security clearances: You may need to restrict access to information based on a user's security clearance. This can impact both the tenant(s) a user has access to and the role configured for that user within a given tenant.
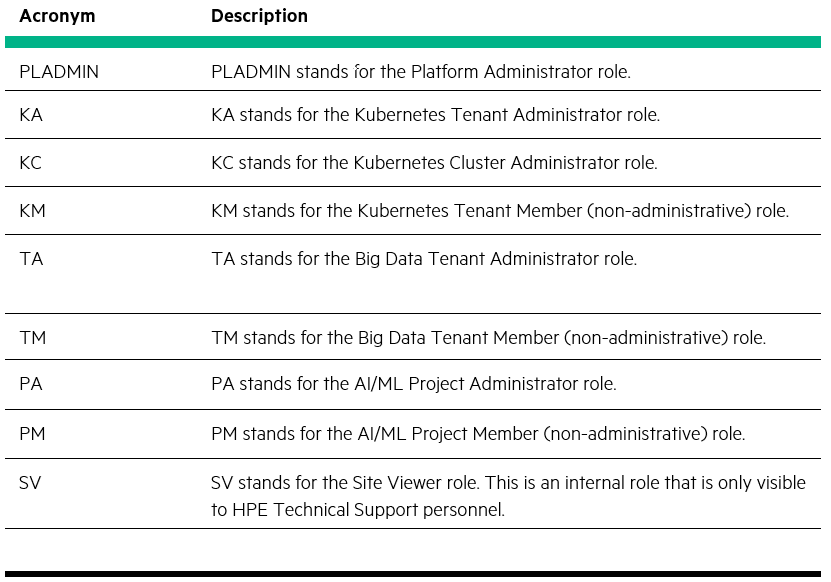
The following table lists the role specific acronyms that is used within HPE Ezmeral Container Platform:
Table 10. HPE Ezmeral Container Platform roles and specific acronyms
# User Management:
Only Platform/Site Administrator will have access to the User Management. Platform/Site adminstroator will have access to add users, delete, assigning roles, and tenants. User Management panel looks like as shown in Figure 52. User Management panel has two tabs (Users and Sessions). Users displays information about username, assigned tenants, authentication type and actions which can performed for the user.
Users can be added/deleted by clicking on Add User/Delete button in the top right corner as shown in the Figure 52.
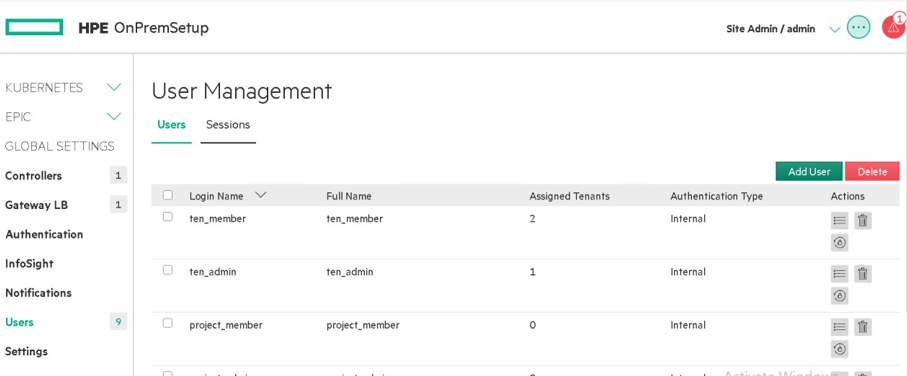
Figure 52. User Management dashboard
Once the user is created, Users details can be found under Users tab. Edit the user to assign tenant/admin and roles. One user can be assigned to multiple tenants.
Figure 53 shows how to assign tenants and roles to the users.
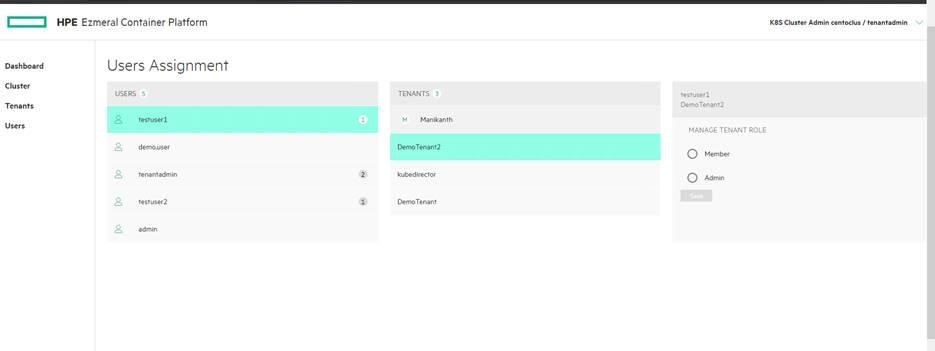
Figure 53. Users Assignment
- Each user must have access to at least one tenant. By default HPE Ezmeral Container Platform provide support for two roles (admin and member). Users created with admin role has full rights to the associate tenant/project/cluster whereas users created with member role has limited access to the associate tenant.
NOTE
In this document only Kubernetes users has been created. EPIC user details are not available.
- Users who are logged in as Kubernetes cluster admin and Kubernetes tenant admin can revoke the access and no longer will not have access to the tenant.
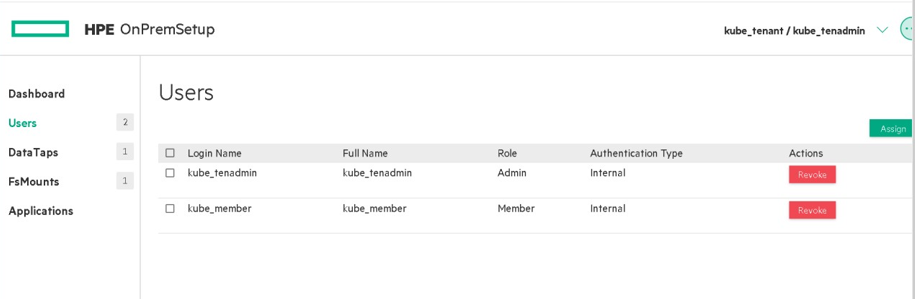
Figure 54. kube_tenant tenant accessible by two users kube_tenadmin and kube_member
As part of invitation, following users has been created
Kubernetes Member Dashboard screen (see Dashboard - Kubernetes Member)
Kubernetes Cluster Administrator Dashboard screen (see Dashboard - Kubernetes Cluster Administrator)
Kubernetes Tenant Administrator Dashboard screen (see Dashboard - Kubernetes Tenant Administrator)
# Kubernetes Web Terminal
HPE Container Platform allows Kubernetes users to access the Kubernetes Web Terminal that includes the HPE Kubectl plug-in, Helm, and access to the Kubernetes tenant FS mounts. The Web Terminal is a KubeDirector application, that is, a stateful Kubernetes set.
To access the Web Terminal:
Log in to HPE Ezmeral Container Platform, and then navigate to the appropriate Kubernetes cluster or tenant according to your credentials and role (Member, Tenant Administrator, or Cluster Administrator.)
Click the green Initialize button that appears at the bottom of most Kubernetes screens within HPE Ezmeral Container Platform.
- The screen will say Waiting for terminal to be ready. This process will take a few minutes if this is the first time you are accessing the Web Terminal because HPE Ezmeral Container Platform must launch a new webterm service pod using the default MapR-based storage.
Once the Web Terminal is ready, click the Launch icon (plus sign) to launch the terminal window.
HPE Ezmeral Container Platform pre-installs kubectl in the Web Terminal environment and also configures the appropriate kubeconfig. This config behaves in the same way as a locally downloaded config, as described in the Role Privileges, below, and in Managing a Kubernetes Cluster via Local Kubectl. You should never need to manually refresh/recreate the config.
# Kubernetes Cluster Administrator
HPE Ezmeral Container Platform users who are logged into a Kubernetes tenant with the Cluster Administrator role can access the Kubernetes Tenant Administrator Dashboard screen by selecting Dashboard in the main menu.
The top of this screen has three buttons that allows you to download the plugins that you need to access Kubernetes pods within a cluster as shown in Figure 55. The buttons are:
HPE Kubectl Plugin: Downloads the HPE installer for the kubectl command line tool for controlling a Kubernetes cluster. User will need to install this application.
Kubectl: Downloads the generic installed for the kubectl command line tool for controlling a Kubernetes cluster. User will need to install this application
Kubeconfig: Downloads the kubeconfig file that configures access to Kubernetes when used in conjunction with either the kubectl command line tool or other clients.
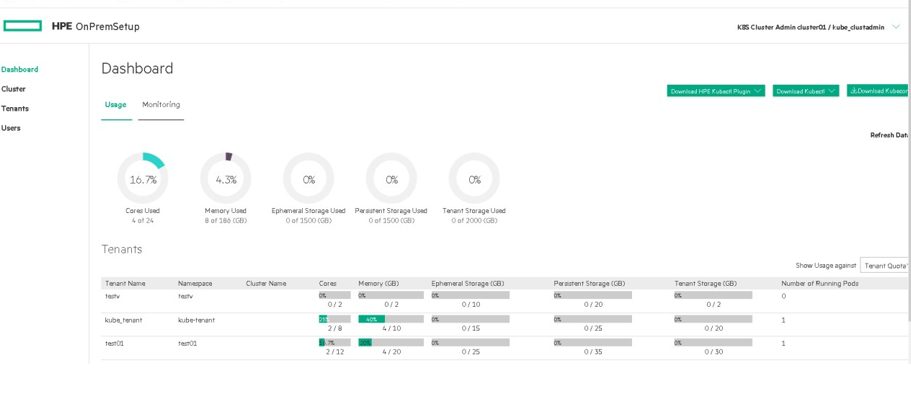
Figure 55. Kubernetes Cluster Administrator logged in into Kubernetes tenant
Kubernetes Cluste Administrator have access to the following tabs.
Dashboard (User has access to usage and monitoring tabs)
Cluster (Display cluster information. More details can be found further in this section)
Tenants (Display tenant information)
Users (Display information about the user. User can revoke the access)
Once user clicks on cluster tab, user will see the following tabs.
Hosts info (Display hosts , role, status details)
Load (Display CPU metrics and memory usage)
Service Status (Display status of services like BD Agent, Disk pressure, Kube proxy, Kubelet, Network, Kube API Server, Kube Controller, Kube Scheduler, FileServer and Mountpoint)
Alerts
When the user logs in as a Kubernetes Cluster Administrator- the cluster panel, load panel and user information is as shown in Figure 56, Figure 57 and Figure 58 respectively.
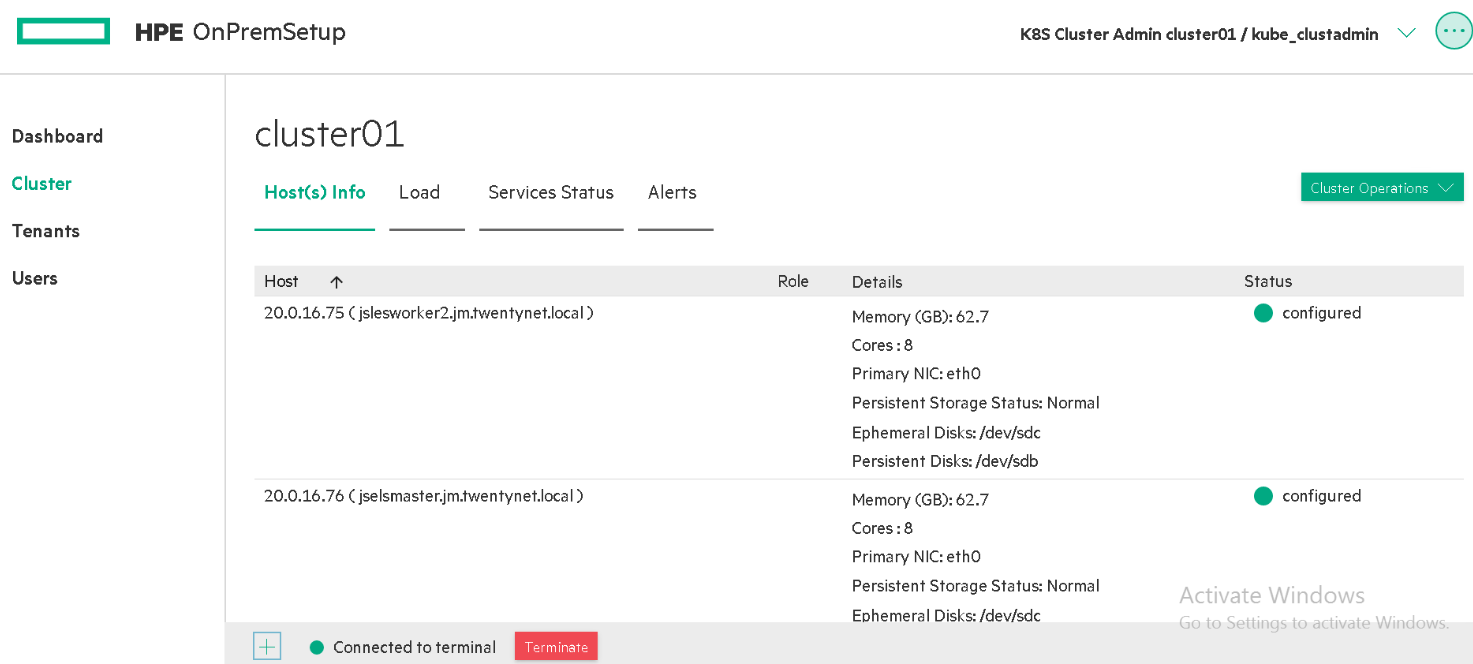 Figure 56. Cluster panel when user logged in as Kubernetes cluster administrator
Figure 56. Cluster panel when user logged in as Kubernetes cluster administrator
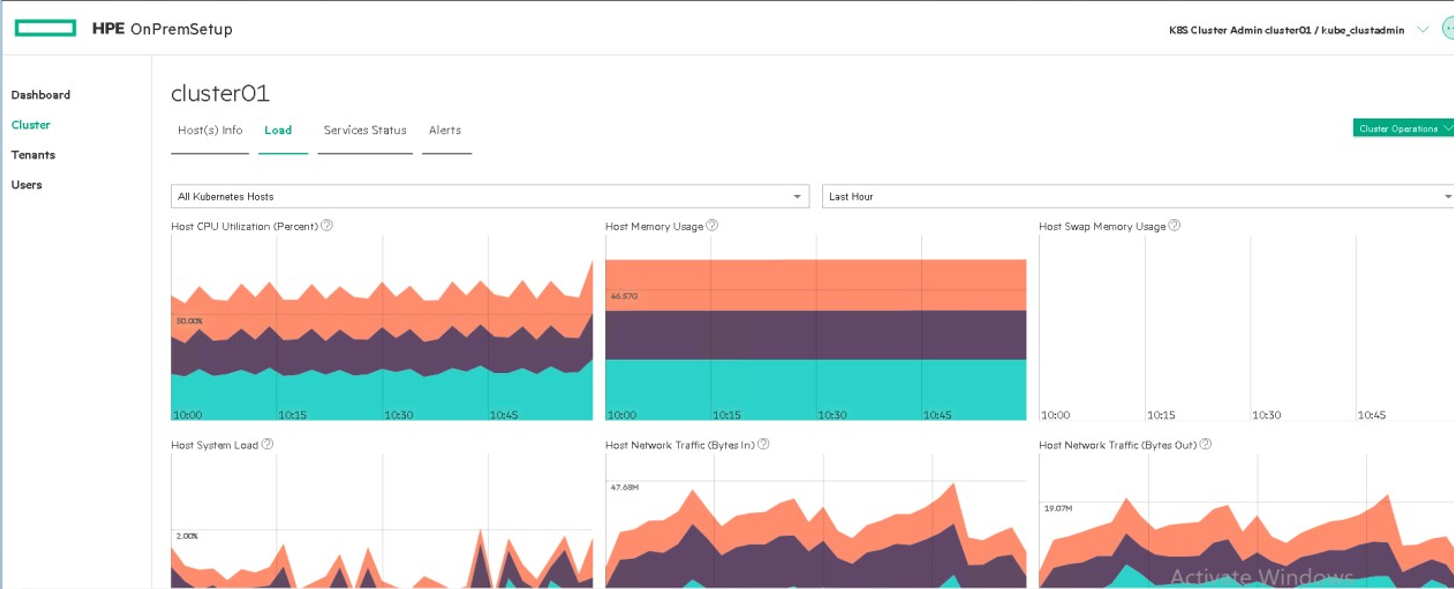 Figure 57. Load panel when user logged in as Kubernetes cluster administrator
Figure 57. Load panel when user logged in as Kubernetes cluster administrator
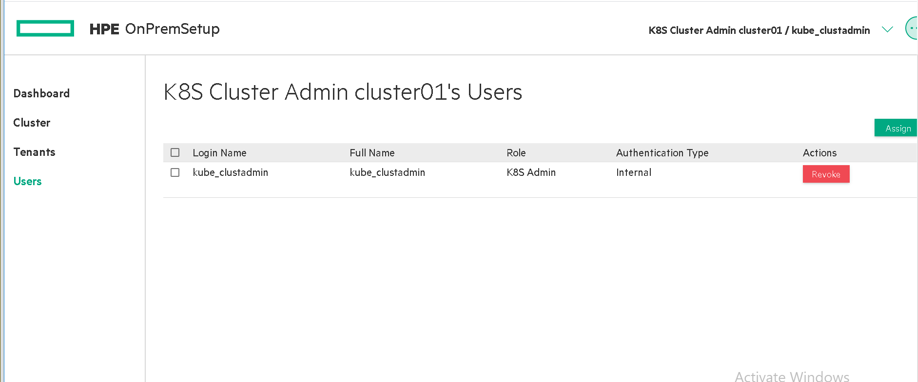 Figure 58. Users information
Figure 58. Users information
NOTE
If the User has a Platform Administrator role or a Kubernetes Cluster Administrator role in the current cluster, then that user will receive system-masters privileges regardless of any explicit tenant role assignments that user may also have.
# Kubernetes Tenant Administrator
- HPE Ezmeral Container Platform users who are logged into a Kubernetes tenant with the Tenant Administrator role can access the Kubernetes Tenant Administrator Dashboard screen by selecting Dashboard in the main menu as show in Figure 59.
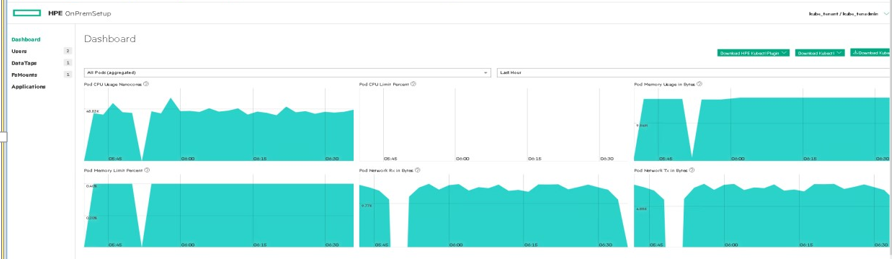
Figure 59. User logged in as Kubernetes Tenant Administrator
Kuberenets Tenant Administrator will have access to the following tabs.
Dashboard
DataTaps
FsMounts
Applications
Users
When the user logs in as a Kubernetes Tenant Administrator- the DataTaps panel and FsMounts panel is as shown in Figure 60 and Figure 61 respectively.
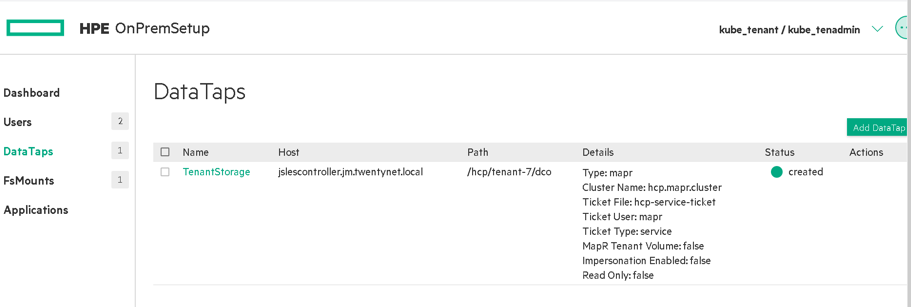 Figure60. DataTaps panel when user logged in as Kubernetes Tenant Administrator
Figure60. DataTaps panel when user logged in as Kubernetes Tenant Administrator
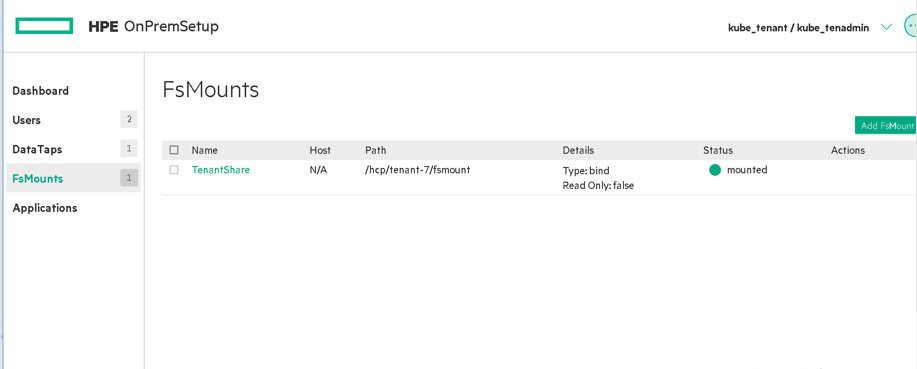 Figure61. FsMounts panel when user logged in as Kubernetes Tenant Administrator
Figure61. FsMounts panel when user logged in as Kubernetes Tenant Administrator
# Kubernetes Member
HPE Ezmeral Container Platform users who are logged into a Kubernetes tenant with the Member role can access the Kubernetes Member Dashboard screen by selecting Dashboard in the main menu
Kubernetes Member will see the following information on Dashboard.
CPU Usage Percent: Percentage of available CPU resources in use.
CPU Use Nanocores: Number of CPU cores in use, in 1/1000ths of a core.
CPU Pod Limit Percent: Percentage of maximum number of pods that are currently running inside the current cluster.
Node Memory Usage Percent: Percentage of available memory being used.
Memory Usage in Bytes: Bytes of memory being used.
Memory Limit Percent: Percentage of memory limit being used.
Network Rx in Bytes: Bytes received over the network.
Network Tx in Bytes: Bytes transmitted over the network.
GPU Utilization (percent): If GPUs are present, displays aggregate GPU utilization in percent.
GPU Memory Usage: If GPUs are present, displays aggregate GPU memory usage in percent.
Kubernetes Member has access to the following tabs as shown in Figure 62.
Dashboard
DataTaps
FsMounts
Applications
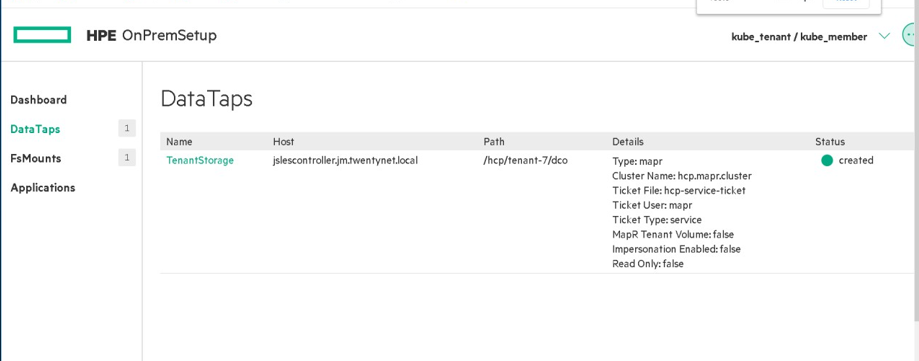
Figure 62. User who logins as Kubernetes Member
By default Kuberenets member would have limited access to the assigned tenant. For example, user cannot get information about resources like secrets, roles, and role bindings. Admin user can grant full access to Kubernetes member. Admin can do this by executing following command.
> kubectl edit hpecptenants.hpecp.hpe.com -n <name_space>
NOTE
Site admin/Platform Administrator can add the resources/grant access to the member user associated with specific tenants using following command.
> kubectl describe ns kube-tenant
> Kubectl edit --n hpecp hpecptenant hpecp-tenant-7
Note
Updating the tenant quotas of cpu, gpu, memory from cli will not reflect in the HPECP UI. Hence we need to change these quotas in the UI only.
Only the platform administrator can create roles. not any other users.